Password Security
1. What are passwords and where it is used?
A password is a sequence of characters used to confirm a user’s identity when logging into email or other Social Media accounts. Most applications and websites require an account to log in, and creating these accounts requires using an email address or phone number in addition to a password or any other authentication method. It is important that your password is strong and unbreakable, thus protecting your account from falling into the wrong hands.
2. What are the risks associated with passwords?
As technology develops and crime pattern develops, you need to be
mindful of what the criterion for a strong password is. Why?
Because hackers use advanced techniques and technology to obtain your
information or hack an app or a website and obtain that database of
credentials, just like the recent Facebook hack in April 2021. The
perceived safety that is common is just to comply with complex password
of 8 characters like having capital and small variations, special
characters, and a number, like a long word or a word being a place, or a
device, or a brand or even P@ssW0rd123. But in fact, that is an example
of a possible weak password that has already been included in the
attacks and probably breached previously and sold in the dark web.
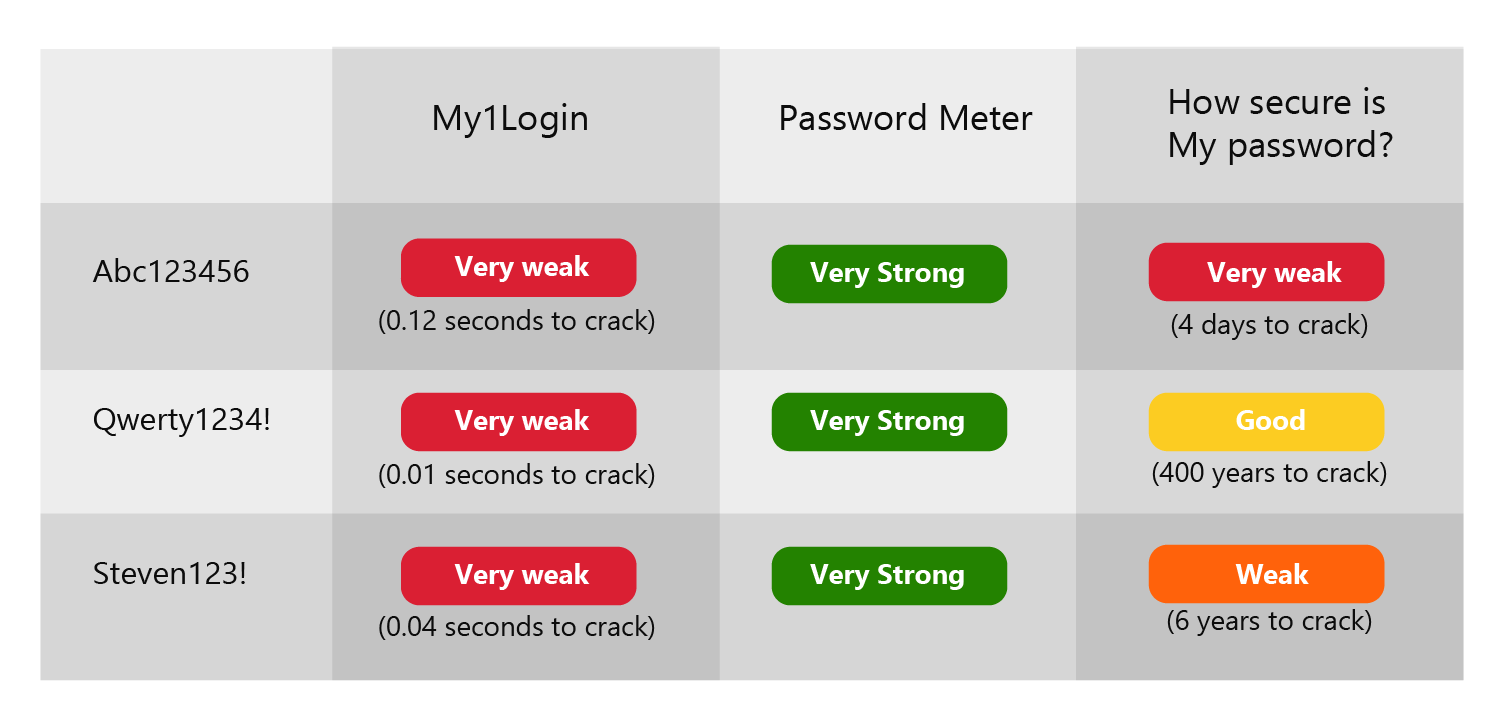
Even if your website is equipped with a password strength-checking tool,
(like the ones below) the results can be inconsistent and inaccurate,
often leading users into a false sense of security.
3. What if your password is Owned?
Your account's security has been compromised if your password is owned. Almost every week, there is a new data breach on a website or service that has been widely published all over the world. It is only natural to wonder if your personal information was compromised in this way. It is possible that cybercriminals have obtained your passwords and email addresses either by targeting you or the websites and apps you use on the internet.
4. Consequences if your account/password is owned?
Identity theft may begin with a hacking of an account using your email address. You may have used the same login credentials on another account to access your credit card information or other sensitive personal data. If your email account falls into the wrong hands, hackers are motivated financially and by the ability of execution of the crime. So, they can use it to buy things in your name, spread malware and continue the act of crime or sell your credentials.
5. How to Know If Your Password is Owned or has Been Breached Online
To check your email accounts for any previous data breaches, you can use the following tools to see if your email accounts have been hacked.
-
';--have i been pwned? - https://haveibeenpwned.com/
-
F-Secure Identity Theft Checker- https://www.f-secure.com/en/home/free-tools/identity-theft-checker
-
AVAST HACK CHECK - https://www.avast.com/hackcheck
-
Google provides a feature called password checkup that can assist you figure out whether your account password has been revealed because of a third-party breach.Google added its own password scanner right into the most popular web browser on the planet, Google Chrome.
The following link will show you how to find out whether your Google account's password has been compromised. Click Here
6. Identifying the Signs/Symptoms of a Password Breach
-
If your password is changed without your knowledge or permission.
-
Emails in your sent folder that you do not recognize.
-
Emails requesting a password reset that were not expected.
-
You receive an email stating that someone signed into your account when you have not done so.
-
Contacts have expressed their dissatisfaction.
-
Unusual IP addresses, devices, and/or browsers activities Unusual IP addresses, devices, and/or browsers activities.
-
You receive an email with instructions for resetting your social media account password, but you do not attempt to do so.
7. When your password is compromised, Here's What You Should Do First
-
Passwords should be reset
Most hackers are interested in your account and account information. If you are having trouble logging in, try resetting your password. Look for an account recovery option if changing your password does not work or the e-mail linked with the account no longer works. If none of the alternatives work to reset the account, you must contact the firm for assistance.
Keep the following points in mind while updating your password
-
It is never a good idea to use a password that is simple to guess. Passwords such as 1234, password, and others are simple to guess.
-
Do not use passwords you have already used.
-
Capital and small Letters, numbers, spaces, and other special characters should all be included in passwords.
-
The length of a password should be at least 12 characters. The longer your password is, the longer it will take for hackers to crack it.
-
Note: If you are using the same password for several accounts (which is not recommended), you will need to change your other accounts’ passwords. Once a hacker has your login and password, they retain it and frequently distribute it, which may be used to breach other accounts.
-
-
Check your account information
If any of your accounts feature shipping information, double-check that it is still your address after you have changed all your passwords. If the account allows third-party programs or applications to access the account (for example, Facebook and Twitter), ensure no third-party applications have access to your accounts that you have not granted permission to. The best suggestion is to remove any software you do not recognize or do not recall downloading.
-
Notify your other contacts of the breach
If your e-mail account or any other account with contacts is compromised, notify your contacts, or notify the support of the app you are using. Hackers frequently use connected accounts to obtain access to other accounts because people are less distrustful of e-mails from people they know.
-
Setup of new accounts
If a hacker has access to your e-mail, they will frequently utilize it to create other accounts. Using your e-mail address, check your inbox, sent items, and trash for any new account alerts. If any new accounts have been established, you can attempt login into them using the reset password tool before deleting them.
-
Check out previous posts
If your Social Media account has been hacked (e.g. Facebook,Twitter), ensure sure no posts or messages have been created in your name. Hackers use your Social Media accounts to transmit spam, malware, and ads on your behalf.
-
Examine your machine
It is conceivable that you or your machine were the source of the assault if the firm that hosts your accounts did not discover or disclose it. Check your computer for spyware and viruses that might be stealing your account information or logging your keystrokes. If malware is discovered on your computer, you should change your account passwords again, since the viruses may have saved your new password.
-
Configure Multi-Factor Authentication
You need to move on the offensive now that you have changed your passwords defensively, analyzed the issue, and put up a fraud alert. You must take the appropriate precautions to avoid being hacked in the future. Multifactor Authentication is one of the most effective ways to secure your account, acting as an additional layer of protection in addition to passwords.
There are several different methods of multifactor authentication. The most commonly used are as listed below
-
MFA via Mobile App: A number of applications like Google Authenticator for MFA are available. These apps create fresh keys on a regular basis, and after entering your password, you must launch the app and fill in the numeric code.
-
Secure Key 2-Factor Authentication: A “secure key” is the newest and most secure way for 2-factor authentication. This USB or Bluetooth key may be kept on your keychain and automatically verifies that you are the real you to your computer or mobile device.
-
8. Password Management: Creating and Handling Strong Passwords
Strong passwords should be always created and handled by users. Passwords are frequently the main line of defense between the users and the sensitive data. Attackers can use a variety of programs to guess or break passwords. Choosing strong passwords and keeping them secure, on the other hand, might make it more difficult for outsiders to get access to your data.
Related Topics
