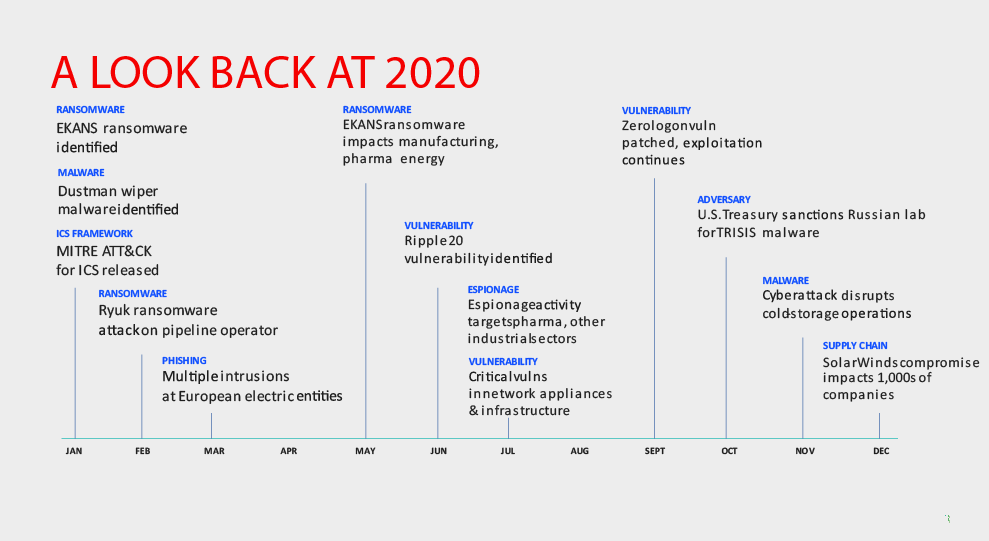
Industrial Control Systems
"Cyberattacks on the global Industrial control systems “ICS” have been
on the rise, and even yet more since the COVID 19 Pandemic - targeting
Critical National Infrastructure “CNI” and utilities specially. The
reason behind this, this is likely due to the increased investment made
by adversaries in targeting ICS over the last five to 10 years, [which]
will continue to accelerate the ICS threat environment.”
-according to Cyber security leader Dragos' 2020 ICS Cyber security Year
In Review report
Introduction
“Industrial control system” ICS refers to a group of control systems and related instrumentation that includes the devices, systems, networks, and controls that are used to operate and/or automate industrial processes. Each ICS is developed to efficiently handle work electronically and performs differently depending on the business. ICS devices and protocols are now found in practically every industrial sector and vital infrastructure, including manufacturing, transportation, Health, energy, and water treatment.
Based on latest alerts by CISA, publicly facing services are a growing target. Asset owners should invest in network detection-based solutions, secure remote access systems, internet facing devices protection, and other security measures suited to their industrial environments. To be effective, these investments must be incorporated into a layered defence strategy within their organization's network.
1. Supply chain attack
When we evaluate the ICS risk and vulnerability landscape, we primarily
look for vulnerabilities and weaknesses in OT networks that may be
exploited by an attacker to accomplish a specific result. However, when
we take a step back from the manufacturing environment, we see another
danger: what if the industrial control system gets hacked before it is
ever put into production? That is where supply chain attack come into
play.
the last decade, awareness of supply chain attacks grew as major
incidents were reported. For example, in the Target security breach
(2013), attackers used stolen credentials from the vendor that provided
the HVAC systems in Target stores in order to access its network and
move laterally until finally stealing bank card and personal information
of millions of customers, resulting in hundreds of million of dollars in
damages for the retailer.
The NotPetya ransomware (2017) was also a supply chain attack, as the
attackers first compromised M.E.Doc, a Ukraininan accounting firm,
poisoning its software updates that were downloaded by victims, allowing
NotPetya to spread around the world. NotPetya affected multinational
corporations such FedEx, Merck, and Maersk, ultimately causing an
estimated $10 billion in damages, making it one of the most expensive
cyber-attacks to date.
Most recently, a supply chain attack trojanizing SolarWinds Orion
software was discovered. This attack was used to distribute the SUNBURST
backdoor. The attack allowed a threat actor to gain access to numerous
organizations around the world as part of SolarWinds' software update
process. The campaign was closed by Microsoft, but the full extent of
the attack's reach and damage is yet to be known.
Finally, when thinking about COVID-19, the pandemic that very well
shaped security risks and cyber-attacks during 2020, we must also take
the vaccines' supply chain into consideration.
Supply chain attacks occur when an attacker gains access to your system
through a third-party supplier or partner, and they can affect any stage
of a product's lifecycle.
Design > Manufacturing> Distribution >Storage Maintenance
In every single one of these steps, there is a risk of an attack
targeting the less secure elements in the chain. This risk complicates
the situation, because the process is not necessarily done entirely in
one geographical area or under the responsibility of a single
organization.
Key topics presented to management should refer to mitigating the
ability of adversaries to interrupt the business continuity through
supply chain attack and providing detailed processes for fast and
effective recovery from an incident—" when addressing the topic of risks
rather than development and business continuity to higher management”.
Most of the vendors adhere to the 27001-2013 standards, but sometimes
that is not the case. Whilst the regulations are taking a change to
incorporate the latter, and we see that small vendors do take that into
practice, it is a good start to consider the following:
-
Since vendors in some cases have virtual access to your organization, consider including your expectations for security controls and periodic auditing within vendor contracts to ensure that your selected suppliers meet the same level of scrutiny as your internal enterprise.
-
Know the risks associated with your third-party partners and suppliers. Questions from you would be: How do they protect your software? Are physical security measures deployed in their facility? You will also find them asking you about the risks you have and contingency plans.
-
Include the supply chain in your response and remediation plan. This step follows the previous- just because you have done the assessment and monitoring does not mean you are risk free, in other words this is managing your overconfidence into the visibility of their supply chain. You should be able to discuss questions like How effectively will they react when a zero-day vulnerability is published affecting your system?
Adherence to the PPT Triad (People, Policies and Technology) can help you improve in cyber defences. However, keep in mind that this is not applicable to all vendors and needs going beyond that approach as the threat landscape is changing and the methodologies are seen to be sophisticatedly simple! The right approach is therefore adding innovation and consistent improvement to each of the 3 factors in the PPT Triad with changes in the process.
2. Threats from malware
Firm employees in ICS workplaces frequently use portable media. Malware can be transferred using removable media such as CD, USB etc. Malware can readily be included in the files on the portable media. After that, the media storage devices with the malicious files can bypass over physical security and infect the ICS system.
3. Attack from the Insider
A dissatisfied control-system technician spies over other technicians to obtain credentials, then logs in to equipment controlling the physical process with the stolen credentials and gives shut-down commands to parts of the physical process, resulting in a partial plant shutdown. This is an attack that is moderately complex. ICS specialists have a solid understanding of how to operate control system components to achieve specific goals, such as a shutdown, but often have a limited understanding of fundamental engineering ideas or safety features built into industrial processes.
4. RANSOMWARE
A dissatisfied control-system technician spies over other technicians to obtain credentials, then logs in to equipment controlling the physical process with the stolen credentials and gives shut-down commands to parts of the physical process, resulting in a partial plant shutdown. This is an attack that is moderately complex. ICS specialists have a solid understanding of how to operate control system components to achieve specific goals, such as a shutdown, but often have a limited understanding of fundamental engineering ideas or safety features built into industrial processes.
-
Common RANSOMWARE
An engineer investigating technical information or browsing internet about ICS equipment unknowingly downloads ransomware in the system. The malware uses vulnerabilities in the downloaded system to propagate and encrypt the workstation. It then spreads to most of the systems on the industrial control system. As a result, most of the systems in the industrial network are encrypted, disabling the control system. The impaired control system cannot bring about a shutdown. In a short time, the plant operator triggers an emergency safety shutdown.
As a result, production will be offline, even after the malware has been eliminated from the control system and the plant has been restarted. -
TARGETED RANSOMWARE
With phishing attacks and malicious attachments, an attacker with good computer skills targets IT insiders and uses Remote Access Tool (RAT) malware to obtain access to the IT network. The attacker uses the RAT to acquire more credentials, eventually getting remote access to a control system for ICS. The attacker infects the ICS with ransomware and demands payment. The site disables all electrical connections between the afflicted plant and outside networks as quickly as possible and attempts to pay the ransom.
-
ZERO DAY RANSOMWARE
A list of zero-day vulnerabilities in operating systems, apps, and firewall sandboxes is accidentally left on an Internet-based command and control center by an intelligence organization which could be used by the threat actors. This gang then generates self-contained malware that spreads by exploiting zero-day vulnerabilities in Windows operating system file sharing software. The malware is simultaneously released on dozens of compromised websites throughout the world, and it quickly spreads encrypting the systems on the network. The malware hops across firewalls to infect and encrypt industrial facilities that can transfer files directly or indirectly with IT networks, causing an emergency shutdown and physical equipment damage.
5. Denial of service
In ICS, both wired and wireless connectivity are used. Attacks on these connections may cause real-time communication between ICS components to be interrupted. Delays of a few seconds in ICS can have a severe negative impact on the operation. Another method of launching a DoS attack is to target individual components, such as PLCs. PLCs are delicate by nature. A heavy port scan can cause the PLCs to crash, causing operations to be disrupted.
6. Technical or physical malfunction
In ICS, both wired and wireless connectivity are used. Attacks on these connections may cause real-time communication between ICS components to be interrupted. Delays of a few seconds in ICS can have a severe negative impact on the operation. Another method of launching a DoS attack is to target individual components, such as PLCs. PLCs are delicate by nature. A heavy port scan can cause the PLCs to crash, causing operations to be disrupted.
7. Threats from terrorists and hackers
Terrorist groups that would like to inflict fear, destruction, and loss of life often attack critical infrastructure. Air traffic control, electrical networks, and nuclear power plants are mostly at risk. Hackers financed by industrial competitors, terrorist organizations, or other malicious actors may cause major damage, resulting in financial losses and tarnish company's reputation.
8. Lack of Network Segmentation
Attackers can gain access to OT systems through an internet-connected OT flat and misconfigured network, as well as firewall features that fail to detect or prevent malicious activity.
9. Web Application Attacks
Traditional Operational Technology (OT) systems, such as human-management interfaces and programmable logic computers, are becoming increasingly networked and accessible via the web-interface from anywhere. Web Application Attacks like Cross-site scripting and SQL injection attacks can compromise unprotected systems.
10. Command Injection and Parameters Manipulation
Attackers can execute arbitrary system instructions on OT systems using invalid data that has not been authenticated as legitimate system traffic.
11. Market Manipulation
To build a foothold on IT networks, an organized crime organization exploits known weaknesses in Internet exposed services. They install RAT tools on the infected system and eventually get Windows Domain Admin access. The attackers infiltrate ICS PCs that trust the IT Windows domain and install RAT software on them. Because the ICS systems are unable to route traffic to the Internet, the attackers route traffic through compromised IT devices using peer-to-peer connections. Attackers then get access to the ICS network and download and examine control system configuration files.
12. Hijacked Two Factor
ICS is mostly protected by best-practice industrial security, malicious
actors often attempt to compromise operations in ICS. As a result, they
create custom RAT malware to bypass anti-virus systems and use social
media research and targeted phishing emails to target support
technicians at the industrial site. The technicians enable malware
attachments and grant the malware administrator capabilities. Rather
than launching the RAT at the industrial site, where it could be
detected by the site's sophisticated intrusion detection systems, the
attackers wait until the technician victim is at home and needs to log
into the industrial site remotely to resolve an issue. The employee then
uses two-factor authentication to log in.
Unfortunately, at this point, the malware has activated, displaying the
technician an error message. The malware then allows attackers to
remotely control the Invisible RDP Window. The technician reconnects
remotely to the industrial site, unaware of the disruption. Attackers
can get into industrial operations if the technician's laptop and VPN
are enabled.
13. Compromised Vendor Website
Cybercriminals break into an ICS vendor's website that is not well-defended. They get the latest versions of the software and study it. The attackers utilize the hacked website to unpack the ICS software's most recent security update and implant a tiny script. The attackers repackage the security update, sign it using the web server's private key, and publish it along with a new MD5 hash. Many sites will download and install the infected update over time. The malicious script is then launched at each target.
14. Hardware Supply Chain
A well-defended industrial site is successfully hacked by a
sophisticated attacker. The attacker steals information about vendors on
the industrial sites supplying computers and servers. Then, the attacker
then gets close to the logistics company's delivery people. When it is
apparent that a new shipment of computers is on its way to the
industrial site, the threat actors break into the delivery van, open the
packages destined to the industrial site, and insert wireless
controllable spy devices into the new equipment.
After the equipment has been put into production, the attackers use
wireless access to infiltrate the physical process through the spy
devices. The attackers ultimately compromise equipment protection
measures, ultimately debilitating the production at the plant.
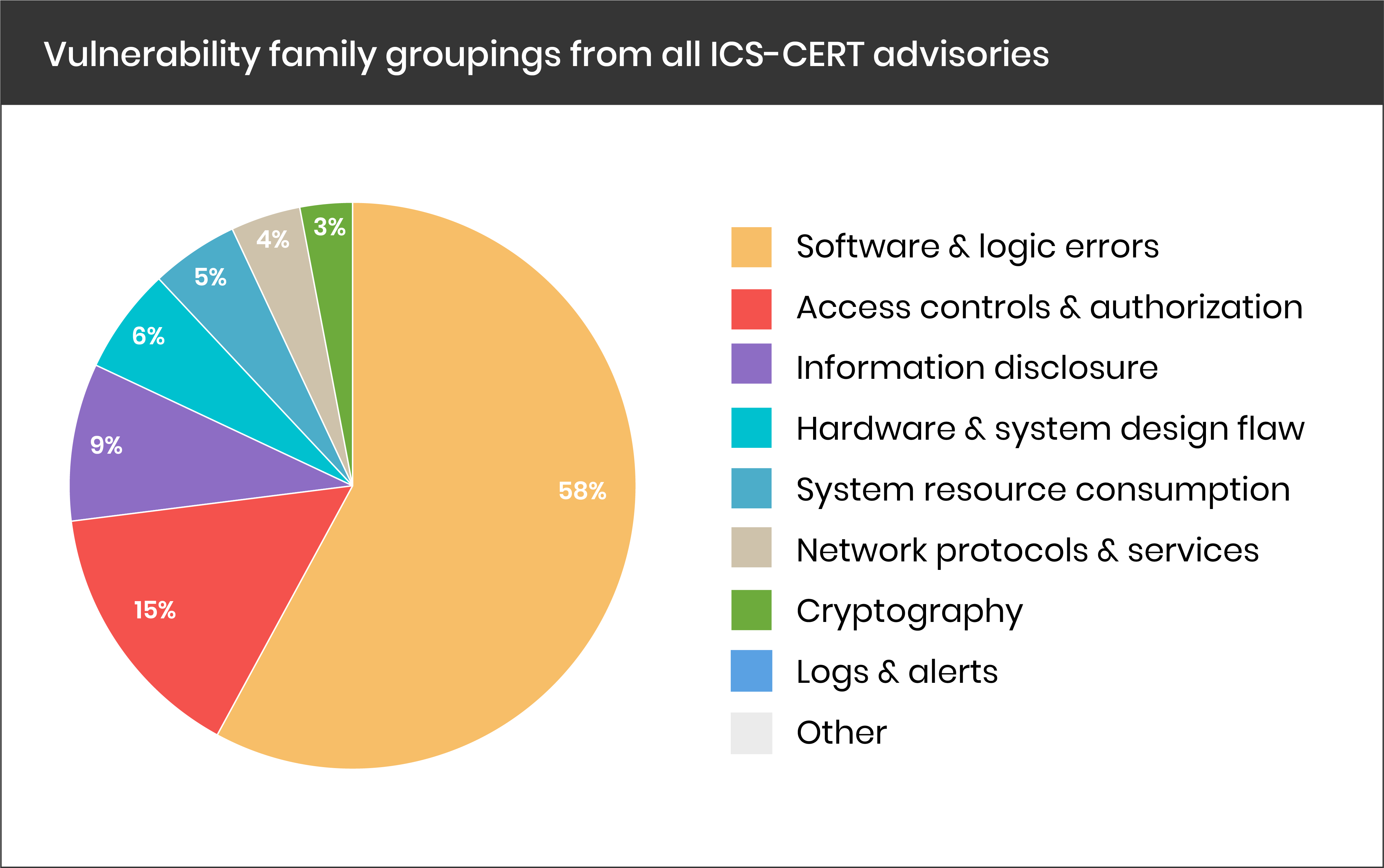
In 2020, the number of ICS vulnerabilities grew even more
According to the industrial Cyber security firm Claroty, the number of
ICS vulnerabilities disclosed in 2020 (893 vulnerabilities) was nearly
25% higher compared to 2019 and close to 33% higher than in 2018. The
company believes this increase is likely the result of heightened
awareness of the risks posed by vulnerabilities in industrial products,
as well as researchers and vendors putting more effort into identifying
and patching security holes.
The company said 61% of vulnerabilities were discovered by third-party
researchers, many of them employed by Cyber security companies. These
research parameters include: Commonality of the platform, device or
equipment Potential damage from an attacker discovering and exploiting a
vulnerability in the product before the vendor patches it.
A comparison of ICS vulnerability data from the 2H (second Half) of
2018, 2019, and 2020 shows the longevity of remote code execution,
read-application data, DoS, and bypass protection mechanisms as the top
four most prevalent impacts.
-
72% of disclosed ICS vulnerabilities are remotely exploitable.
-
47% of disclosed ICS vulnerabilities affect Levels 1 and 2 of the Purdue Model.
-
46.32% of vulnerabilities found affect the Basic Control (level 1) and Supervisory Control (Level 2) Level of the Purdue Model.
-
14.7% of vulnerabilities found affect multiple types of products (operating at various OT purdue model levels, IoT, and network device). This category vulnerabilities in third-party components.
-
89.98% of vulnerabilities dont require special conditions to exploit, and an attacker can expect repeatable success every time.
-
In 76.39% of the vulnerablities, the attacker is unauthenticated prioe to attack and doesn't require any access or privileges to the target's settings or files.
-
For 78.17% of the vulnerablities, there is no requirement for user interaction.
-
78.92% of the vulnerablities, that don't require user interaction are remotely exploitable.
-
For 80.95% of the Supervisory Control vulnerabilities, user interaction is needed if exploiting via a local attack vector. This indicates a playground for social engineering attack vectors.
-
76% of disclosed ICS vulnerabilities do not require authentication for exploitation.
IN Summary, The Claroty Research Team's approach was inclusive of the
assessment of events and trends that likely helped shape the ICS risk and
vulnerability landscape to a degree during the 2H 2020.
When it comes to operating systems, embedded devices, systems-on-a-chip,
networking equipment, OT devices and etc, and as often that happens with
third-party vulnerabilities; the scope of affected devices and vendors is
unclear and is being updated on an ongoing basis.
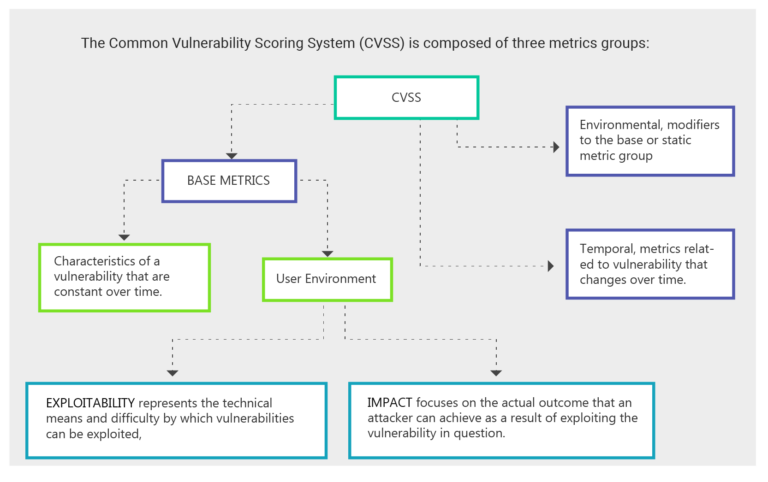
ICS defenders need to evaluate the severity of a vulnerability further than
just its Common Vulnerability Scoring System (CVSS) score- latest being
CVSSv3. This is often left out by security admins in ICS and other IT
environments, or the knowledge is “on the surface”. The lack of
understanding and knowledge behind this leaves an unfinished threat
landscape analysis, vendor dependent operations and huge risk.
Security weaknesses—or Common Weakness Enumerations (CWEs)—manifested in the
ICS vulnerabilities disclosed during Second Half of the year 2020, help
explain why most of the vulnerabilities have CVSS scores categorized as
either high or critical. The top five most prevalent CWEs are all ranked
highly on The MITRE Corporation's 2020 CWE Top 25 Most Dangerous Software
Errors list due to their relative ease of exploitation and ability to enable
adversaries to inflict serious damage.
If we dissect it further in the world Cyber security, the attacker has a
specific range of vulnerabilities to explore on a targeted ICS environment
which usually do not carry a weight in complexity. The attackers, taking for
example an APT GROUP, collectively examines one or more attack vectors in
the orchestration, -ways were in direct user interaction is not needed or
has been previously established.
71.49% of the vulnerabilities are exploited through a Network Attack Vector
and are remotely exploitable. This emphasizes the importance of protecting
remote access connections and internet-facing ICS devices. Behind remote
code execution RCE is a clear second tier of potential impacts: allowing an
adversary to read application data, cause DoS, bypass protection mechanisms,
or gain privileges and assume identity.
Another key consideration is that attackers' dependence on user interaction
shows the importance of awareness and protection against social engineering
tactics among workers with access to critical assets, such as HMIs, SCADA,
and engineering stations. That was exemplified via the percentage in
vulnerabilities happening at the supervisory control level wherein the local
attack vector is dominant.
Recommendations:
Quick tips:
-
Increase OT Network visibility
-
identify and Prioritize Crown Jewels
-
Boost Incident Response capabilities
-
Validate Network Segmentation
-
Separate and OT Credential management
Ensuring a safer tomorrow, proactively
Cyber security governance & risk management
-
Determine the organization's threats.
-
Keep an inventory of all ICS assets, including hardware, software, and supporting infrastructure technologies.
-
Develop Cyber security policies, procedures, training, and educational materials applicable to the organization's industrial control system (ICS).
-
Develop and practice incident response procedures that integrate information technology and operational technology processes.
Human element
-
Issue policies outlining ICS security standards, including expected behavior, and required controls.
-
Issue procedures outlining how personnel should securely manage ICS.
-
Train IT and OT operators, as well as security personnel, to identify indicators of potential compromise and the steps they should take to ensure the success of a cyber investigation.
-
Promote a culture of dialogue and information exchange among security, information technology, and operations technology personnel.
Network Architecture
-
When possible, use network segmentation.
-
Develop an ICS network topology with multiple layers, with the most critical communications taking place in the most secure and reliable layer.
-
Whenever possible, use one-way communication diodes to prevent external access.
-
Construct demilitarized zones (DMZ) to create a physical and logical subnetwork that functions as an intermediate for connected security devices to avoid exposure.
-
Use dependable and secure network protocols and services whenever possible.
Physical security
-
Set up alerting systems for device manipulation, such as power removal, device resets, and cabling alterations, and lock down field electronics.
-
Make sure that only authorized people have access to controlled spaces containing ICS equipment.
-
Control logical and physical access to ICS equipment and facilities by utilizing multi-factor authentication, guards, and obstacles.
ICS Network & perimeter security
-
Set up firewalls to manage traffic between the ICS network and the corporate IT network.
-
Utilize IP geo-blocking as needed.
-
Make the remote access process more difficult to reduce risk to an acceptable level.
-
Use jump servers to act as a central authorization point between ICS network security zones.
-
Avoid allowing remote persistent vendor or employee access to the control network.
-
Catalog and monitor any remote network connections.
Security monitoring
-
Estimate the baseline of ICS normal operations and network traffic.
-
Configure Intrusion Detection Systems (IDS) to generate alarms for any ICS network traffic that is not typical.
-
Track and monitor audit trails in ICS critical areas.
-
Configure Security Incident and Event Monitoring (SIEM) to monitor, analyze, and correlate event logs from all over the ICS network to detect intrusion attempts.
Host security
-
Encourage a patching and vulnerability management culture.
-
Test all updates/patches in off-line scenarios before deploying them.
-
Application whitelisting should be implemented on human-machine interfaces.
-
Tablets and smartphones as field devices should be security hardened.
-
Follow a systematic approach to replace outdated/end of life software and hardware.
-
After testing, disable unneeded ports and services on ICS devices to ensure that they do not interfere with ICS function.
-
Configure and test system backup and recovery procedures.
-
Configure ICS protocol encryption and security.
Supply chain management
-
Adjust the ICS procurement process to include Cyber security as a major factor in scoring and assessment.
-
Invest in secure ICS products up front, assessing security against current and potential risks across the product's expected lifecycle.
-
For all outsourced services, establish contractual agreements that assure adequate incident handling and reporting, interconnection security, and remote access standards and protocols.
-
When dealing with a cloud service provider, keep ICS information integrity, security, and confidentiality in mind.
-
Use test laboratories to check vendor-supplied software for harmful code and problems before production deployment.
MYTHS to be cleared
Four Myths About Industrial Cyber security
-
Myth 1
My industrial network is secure since it is physically isolated and not connected to the Internet.
Ten years ago, this statement might have been true. Many IIoT gadgets, on the other hand, are now directly connected to the Internet, circumventing traditional IT security levels. Why do so many IIoT devices need to connect to the Internet in the first place, is a topic that is frequently questioned. The fundamental reason for this is that IIoT or Industry 4.0 systems require vast amounts of data to be analysed. Because the data sources may not be in the same area, you will need to connect your systems to the Internet to send the data to a distant server.
Your industrial control systems (ICS) or industrial networks may be vulnerable to unauthorized connections even if they are not connected to the Internet. For example, a third-party vendor or an automation expert may update systems by connecting unapproved laptops or USB drives to do routine maintenance or troubleshooting, exposing the ICS to unsecured access, and increasing the vulnerability of ICS devices. -
Myth 2
Because hackers are unfamiliar with ICS, PLCs, and SCADA systems, my network is safe or less interest is taken in industrial sectors.
Since 2010, many sophisticated cyberattacks have attacked ICS networks, including Stuxnet (which targeted PLCs) and Industroyer (targeting circuit breakers). Malware aimed at industrial control equipment has also been discovered. This pattern demonstrates that hackers are shifting their emphasis to industrial sectors like oil and gas, energy, and manufacturing, implying that assaults on these industries will likely rise in the future. -
Myth 3
Because my network is too tiny to be targeted, it is safe.
Internal breaches are frequently caused by trusted users, employees, and external contractors with network access. Human mistake or a malfunctioning gadget are frequently the causes of unintended breaches, regardless of the size of your firm.
Even though these attacks are unintended, they can cause significant harm and financial losses to your company. -
Myth 4
My industrial network is already protected by a firewall; thus, it is safe.
Although firewalls constitute the initial line of defence, they are not 100 percent effective. Furthermore, because most firewalls are not built for industrial protocols (such as Modbus TCP, EtherNet/IP, and PROFINET), they may block important industrial protocols and shut down industrial control systems if not configured properly. Simply said, firewalls alone will not provide total safety for ICS networks. Instead, to secure crucial control devices, manufacturing lines, and the whole plant, industrial firewalls should be used in conjunction with layered defences (the defence-in-depth method). In addition, to guard against cyberattacks, industrial equipment should be updated with security updates on a regular basis.
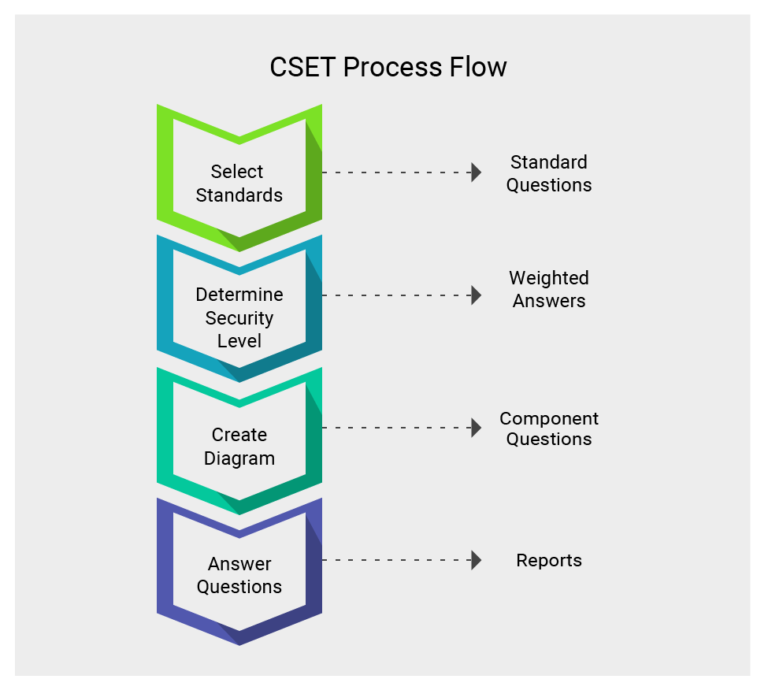
Cyber Security Evaluation Tool
The Cyber Security Evaluation Tool (CSET®) provides a systematic,
disciplined, and repeatable approach for evaluating an organization's
security posture. It was designed to help asset owners identify
vulnerabilities and improve the organization's overall Cyber security
posture by guiding them through a series of questions that represent
network security requirements and best practices.
Users can evaluate their own Cyber security stance using many recognized
government and industry standards and recommendations.
The CSET is a stand-alone desktop software tool that enables users to
assess their network and ICS security practices against recognized
industry and government standards, guidelines, and practices. The
completed CSET assessment provides a prioritized list of recommendations
for increasing the Cyber security posture of an organization's ICS or
enterprise network and identifies what is needed to achieve the desired
level of security within the specific standard(s) selected.
Security Standards
-
DHS Catalog of Control Systems Security: Recommendations for Standards Developers, Revisions 6 and 7 NIST SP800-82
-
NIST SP800-53, revision 3
-
NRC Regulatory Guide 5.71 CFATS Risk Based Performance Standard (RBPS) 8
-
NERC CIP-002-009 revisions 2 and 3
-
ISO/IEC 15408 revision 3.1
-
DoDI 8500.2
-
Consensus Audit Guidelines 2.3.
-
After the user selects the applicable standard(s), CSET generates questions that are specific for those requirements.
CSET was developed under the direction of the Department of Homeland
Security (DHS) Control Systems Security Program (CSSP). Open-source CODE
(for the software) is available in GIT HUB, you can develop the tool or
customize it according to your environment.
https://github.com/cisagov/cset
>> Github software installation ( both standalone & enterprise, Steps for
installing the software package )
Disclaimer
(Bahrain NCSC website URL to this PAGE) contains information items that are supplied “as is” for informative purposes only. The NCSC – BH makes no representations or guarantees about the material presented below. The NCSC-BH does not recommend or support any commercial product or service, whether mentioned in this product or not.
